SOC 2 compliance is an important step for businesses to take in order to ensure their customers’ data is being handled in a responsible and secure manner. By achieving SOC 2 compliance, businesses can certify they’ve put the necessary safeguards and processes in place to protect customer data.
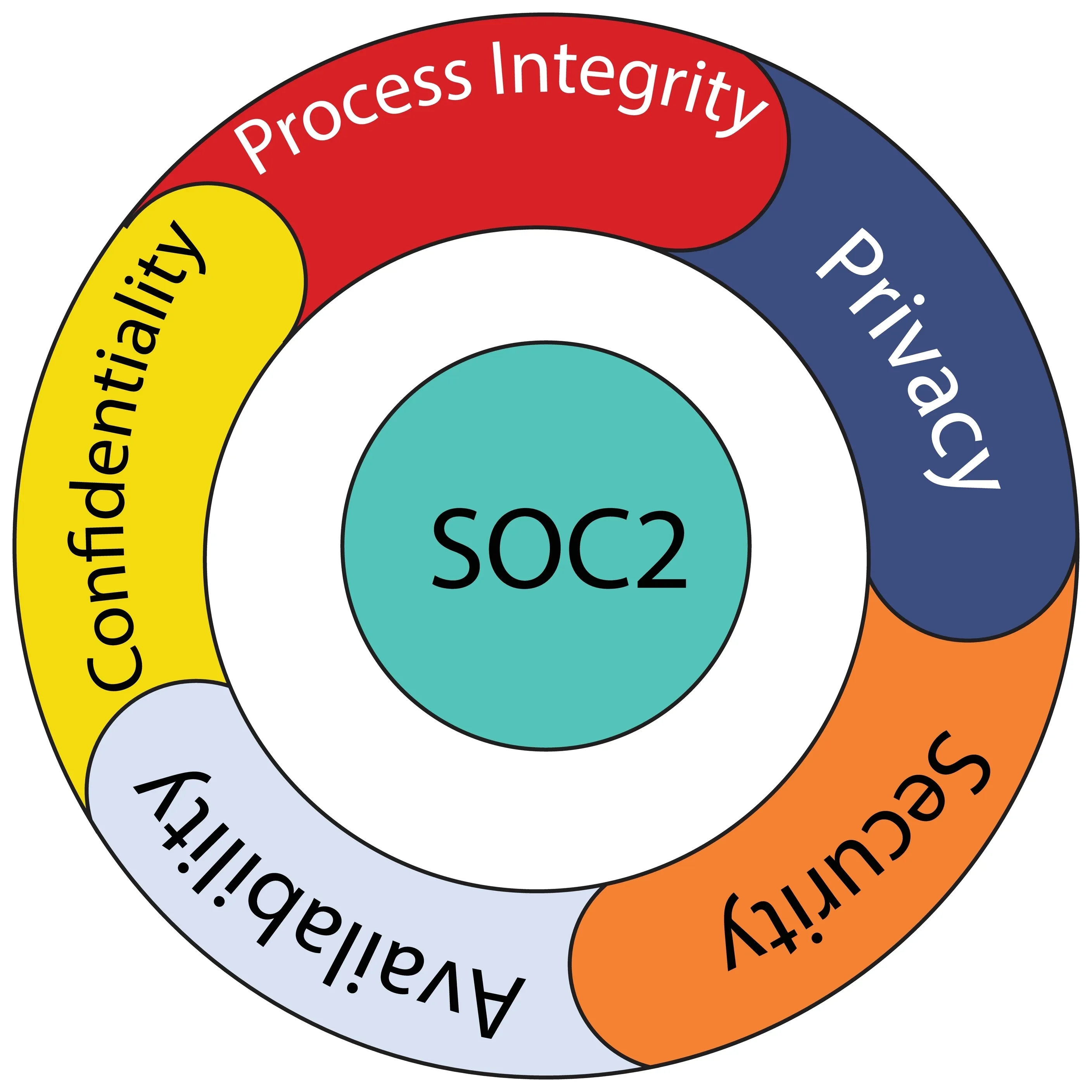
But what is SOC 2 compliance? In short, it’s a voluntary compliance standard developed by the American Institute of Certified Public Accountants (AICPA). It’s based on five trust services principles — security, availability, processing integrity, confidentiality, and privacy.1 Let’s take a closer look at SOC 2 compliance.
Why SOC 2 Compliance Matters
Data security is more important than ever, and businesses that want to ensure their customers’ data is handled in a responsible and secure manner should aim for SOC 2 compliance. SOC 2 compliance is an important step in demonstrating that a business takes data security seriously and can help ensure that customers’ data is protected.
SOC 2 compliance helps businesses put in place the necessary safeguards to protect their customers’ data. The SOC 2 standard covers the five key areas of security, confidentiality, privacy, availability, and processing integrity. By achieving SOC 2 compliance, businesses can show their customers that they take data security seriously.
SOC 2 certification is based on a set of guidelines that provide a framework for measuring customer data security, privacy, and confidentiality. To achieve SOC 2 compliance, businesses undergo an evaluation by an independent auditor. Data security is essential for businesses, and SOC 2 compliance can help companies build customer trust.
 Tea Talk/Shutterstock
Tea Talk/ShutterstockFive Trust Service Principles of SOC 2 Compliance
As previously mentioned, the five trust service principles of SOC 2 compliance are security, availability, processing integrity, confidentiality, and privacy. Each of these principles is important in ensuring that customer data is handled responsibly.
Security is key in preventing unauthorized access to data, while availability ensures that data is accessible as stipulated by the agreed terms of use. Processing integrity guarantees that system processing is complete, accurate, timely, valid, and authorized.
Then there’s confidentiality, which protects information from unauthorized access. Encryption and firewalls can be a part of ensuring confidentiality. Finally, privacy safeguards customers’ personal data from being collected or used without consent.2
SOC 2 Audits
An SOC 2 audit is a detailed review of how a business handles and protects its customers’ data. The audit is conducted by an independent third party, and the results are used to determine if the business meets the requirements for SOC 2 compliance.
The main goals of an SOC 2 audit are to assess the security, availability, and confidentiality of the data that businesses process and store. The audit also looks at how well the business protects against unauthorized access, alteration, or destruction of data.
Benefits of Achieving SOC 2 Compliance
SOC 2 compliance can give your company a competitive advantage. With this in mind, the benefits of achieving SOC 2 compliance include:
- Increased trust and confidence from customers
- Enhanced brand reputation
- Protection against data breaches and other cyber threats
- Compliance with legal and regulatory requirements
- Improved operational efficiency
- Better risk management and control
And, of course, the peace of mind that comes with knowing your customers’ data is being handled securely. It benefits both you and your customers.
SOC 1 vs. SOC 2
There are key differences between SOC 1 compliance and SOC 2 compliance. On the one hand, SOC 1 compliance is focused on ensuring that financial data is protected. SOC 2 compliance, in contrast, is focused on protecting all types of customer data.3
So, the scope of an SOC 2 audit is broader than an SOC 1 audit. Much like an SOC 2 audit, an SOC 1 audit is completed by a third-party CPA firm. An SOC 1 report may be mandatory if your services impact the financials of your company’s customers.4
Importance of Achieving SOC 2 Compliance
Achieving SOC 2 compliance is important for businesses because it shows that they take data security and privacy seriously. By adhering to the five trust service principles of SOC 2 compliance, businesses can ensure that customer data is being handled securely.
If you want to improve your data security posture and make sure your customers’ data is protected, then achieving SOC 2 compliance should be among your top priorities. That’s because it’s a critical framework for technology and cloud computing companies.